Tor Browser – 2021 Ultimate Guide
If you're wondering what Tor is - and if you're here, chances are - then you've come to the right place. Tor is short for The Onion Router, and we'll briefly explain the meaning of that name. The first thing to know is that Tor is a way to hide your internet usage, but is completely different from a VPN. They can be used together, a topic we will also discuss here.
Tor was originally developed by the US Navy with the aim of protecting US government communications during Secret Service operations. It is now a non-profit organization whose purpose is to research and develop online privacy tools. Basically, the Tor network hides your identity by passing your internet traffic over several Tor servers (which are actually different computers).

Tor is a gateway to the Deep Web, or Dark Web, where the vast majority of the Internet resides. A popular analogy to explain what is searchable by standard search engines compared to what is in the Deep Web is that of the tip of an iceberg; the portion of the iceberg below the surface is the Deep Web. These can be websites that are accidentally or intentionally not registered with one of the search engines. An example of this is Silk Road, the online drug-trafficking market that closed down a number of years ago, which could not be accessed through normal browsers and search engines like Google.
Tor is also very popular with journalists, as well as activists living or working in countries with internet restrictions. Tor is one way to get around this censorship. It's also good for whistleblowers like Edward Snowden, who released information through Tor.
How does Tor work?
To use Tor, you need to download and install the Tor Browser, which you can use instead of Chrome, Firefox, or whatever browser you normally use. Everything you do on this browser is then shielded from the prying eyes of the government, hackers, Google Ads and other advertisers. Your data is bundled in encrypted packets before entering the Tor network. Then Tor extracts the header portion of these packets, which can be used to learn things about the sender. This is information such as the source, size, destination and timing of the packet. Then Tor encrypts the rest of the information, which a normal internet connection cannot do. Finally, the encrypted data is sent randomly across many different servers (called relays). Each server then decrypts and re-encrypts just enough of the data to know where it came from and where to go. The encrypted address layers used to anonymize data packets sent over the Tor networkare like an onion, hence the name. The image below is a good (albeit very simplified and in English) explanation of how Tor works.
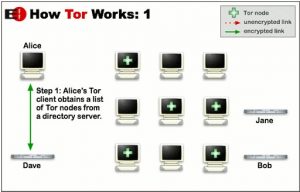
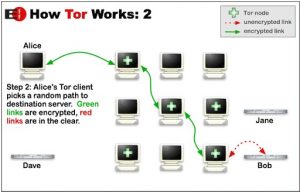
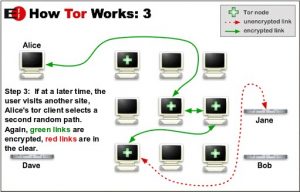
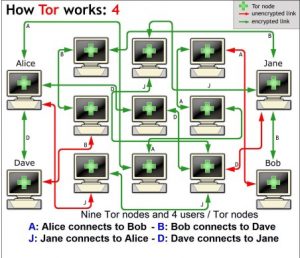
What are the disadvantages?
Tor's biggest, and most immediately noticeable drawback is its performance. The fact that the data goes through a lot of relays makes it very slow, especially when it comes to audio and video. It's also important to know that you don't make yourself 100% invulnerable with Tor . In fact, many people believe that Tor is fairly easy to hack because the exit node (the last relay before your information reaches its destination) can see your traffic if the site you're visiting doesn't use SSL (look for HTTPS instead of just HTTP). Plus, government agencies can see if you're using Tor, so even if they can't see what you're doing, it's a red flag for them.
Use TOR with VPN
Tor and VPN can be used in combination with each other, although the operation is a bit complex: you can use “Tor-through-VPN” or “VPN-through-Tor”, and there is a big difference between the two configurations. We won't go into too much detail but will explain some of the differences. Before we do this though, be aware that regardless of the settings for this, it will significantly reduce your performance as both Tor and VPN slow down internet speed. Combining the two makes this effect even greater.
With Tor-through-VPN , the path is your computer > VPN > Tor > internet . The main advantage of this is that your ISP won't know you're using Tor, although it may know you're using a VPN. In addition, the Tor entry node does not see your IP address, which provides a good extra layer of security. This configuration has the disadvantages that your VPN knows your real IP address , and you have no protection against malicious Tor exit nodes (the non-SSL websites we mentioned above).
With VPN-through-Tor , the path is your computer > Tor > VPN > internet . This configuration, while more secure, requires you to configure your VPN to work with Tor. The benefits to this setup are many. First, the VPN provider cannot see your real IP address, but sees the IP address of the Tor exit node. If you want to go that far, pay with Bitcoin via the Tor browser, meaning the VPN provider really can't identify you, even if it keeps logs. The next benefit is protection against malicious Tor exit nodes, as your data is encrypted by the VPN. This also has the added effect of bypassing some of the blocks on Tor exit nodes (censorship) that exist with the Tor-through-VPN setup.
How to use Tor
The first thing to do to use Tor is to download the Tor browser. This is actually a modified version of Firefox. From here you can take precautions to verify the package signature . This ensures that anyone with an enemy who might try to get them to use an evil version has the correct version.
The next step is to install the Tor browser. It doesn't install like a normal program because it automatically uses your desktop as the destination. This is because Tor is standalone software that doesn't integrate into Windows like usual programs, allowing you to run the browser anywhere, such as from a USB drive. To change the installation location, click Browse and select the desired location. After that, the installation process is just like any other.
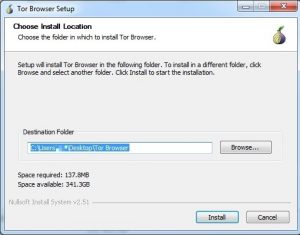
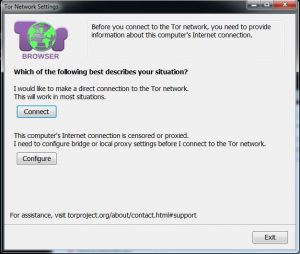
After the browser is installed, a folder called Tor Browser is created where your installation destination is set. Inside it, you'll see Start Tor Browser . Click on it and you will be given the option to connect directly to the Tor Network or to configure proxy settings first. For most, the direct connection option is sufficient. If you're using the VPN-through-Tor method , if you're using a proxy, or if you're on a network that's censored or monitored, you'll need to configure manually with the second option.
Once you're in the Tor Browser, make sure you're connected correctly by going to an IP address checker like whatsmyip.org. If you don't see your original IP address, you're well connected!
Once you're in, there are some tips we recommend you follow:
- Do not go to HTTP websites, only to sites that HTTPS Tor is just a traffic router and encrypts all traffic within the Tor network. However, it does not encrypt traffic outside the Tor network. This leaves you vulnerable as soon as your traffic reaches the exit nodes, as it is unencrypted there. That's why you should always use end-to-end encryption like SSL or TLS, as well as visit sites that use HTTPS. It is also wise to consider using the HTTPS Everywhere plugin .
- Do not use P2P traffic in Tor . Tor is not built for peer-to-peer file sharing and will likely be blocked by many exit nodes. Using P2P traffic on Tor slows down other users' browsing and threatens your online anonymity if BitTorrent customers send your IP address to the BitTorrent trackers and other colleagues.
- Always delete cookies. You can use an add-on such as Self-Destructing Cookies to automatically delete cookies.
- Do not use a real email address. If you send an email, and you use your real email address while using Tor, it's like "going to a masquerade ball, but with a name tag on your costume."
- Don't use Google . Google is notorious for collecting information about users' browsing habits and search data in order to increase their advertising revenue. Use search engines like DuckDuckGo instead .
Finally about Tor
Personal privacy is increasingly at stake as the government, hackers, and even our beloved Google have gotten more sophisticated ways to hack and track us. Tor is an excellent step to be anonymous on the internet, even with its known flaws and vulnerabilities. However, it is only one piece of the puzzle, and other precautions must be taken if you really want to protect yourself. You should think carefully about how you navigate the internet.
If you really want to protect yourself, consider one of the VPNs below in combination with the Tor browser.
