Configuring WireGuard on a Mikrotik router running OpenWrt
In most cases, connecting a router to a VPN is not difficult, but if you want to protect your entire network while maintaining optimal connection speed, then the WireGuard VPN tunnel is the best solution .
Mikrotik routers have established themselves as reliable and very flexible solutions, but unfortunately there is still no support for WireGuard on RouterOS and it is not known when it will appear and in what version. Recently it became known that the developers of the WireGuard VPN tunnel have proposed a set of patches that will make their VPN tunnel software part of the Linux kernel, we hope this will contribute to the implementation in RouterOS.
But in the meantime, unfortunately, to configure WireGuard on a Mikrotik router, you need to change the firmware.
We flash Mikrotik, install and configure OpenWrt
First, you need to make sure OpenWrt supports your model. To see how the model matches its marketing name and image , visit mikrotik.com .
Go to the openwrt.com website in the firmware download section .
For this device, we need 2 files:
downloads.openwrt.org/releases/18.06.2/targets/ar71xx/mikrotik/openwrt-18.06.2-ar71xx-mikrotik-rb-nor-flash-16M-initramfs-kernel.bin|elf
downloads.openwrt.org/releases /18.06.2/targets/ar71xx/mikrotik/openwrt-18.06.2-ar71xx-mikrotik-rb-nor-flash-16M-squashfs-sysupgrade.bin
You need to download both files: Install and Upgrade .
1. Configuring the network, booting and configuring the PXE server
Download the latest version of Tiny PXE Server for Windows.
Unpack it into a separate folder. In the config.ini file add the rfc951 = 1 parameter to the [dhcp] section . This parameter is the same for all Mikrotik models.
Moving on to the network settings: you need to register a static IP address on one of the network interfaces of your computer.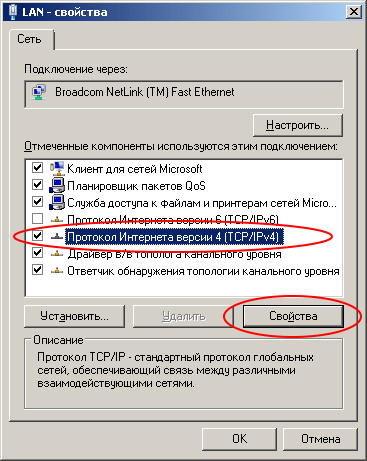
IP address: 192.168.1.10
Netmask: 255.255.255.0

Run Tiny PXE Server as Administrator and select the server with the address 192.168.1.10 in the DHCP Server field. On some Windows versions, this interface may appear only after Ethernet connection. I recommend connecting a router and immediately switching the router and PC using a patchcord. Press the button "..." (bottom right) and indicate the folder where you downloaded the firmware files for Mikrotik. Choose a file whose name ends with "initramfs-kernel.bin or elf"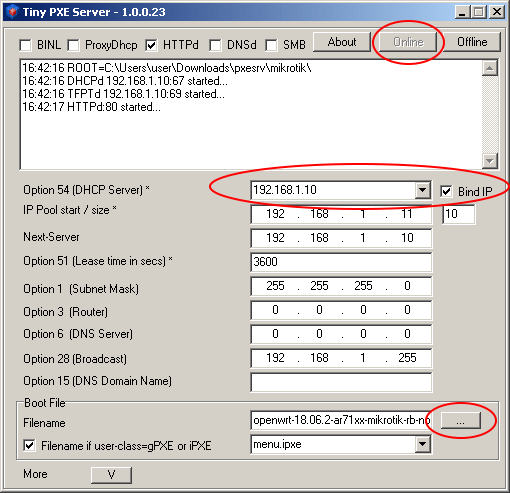

2. Booting the router from the PXE server
We connect the PC with a wire and the first port (wan, internet, poe in, ...) of the router. After that, we take a toothpick, stick it into the hole with the inscription "Reset".
Turn on the power of the router and wait 20 seconds, then release the toothpick.
Within the next minute, the following messages should appear in the Tiny PXE Server window:
If the message appears, then you are in the right direction!
Restore the settings on the network adapter and set to obtain the address dynamically (via DHCP).
Connect to the LAN ports of the Mikrotik router (2 ... 5 in our case) using the same patchcord. Just switch it from port 1 to port 2. Open the 192.168.1.1 address in your browser.
Enter the administrative interface of OpenWRT and go to the menu section "System -> Backup / Flash Firmware"
In the subsection "Flash new firmware image" click on the button "Select a file (Browse)".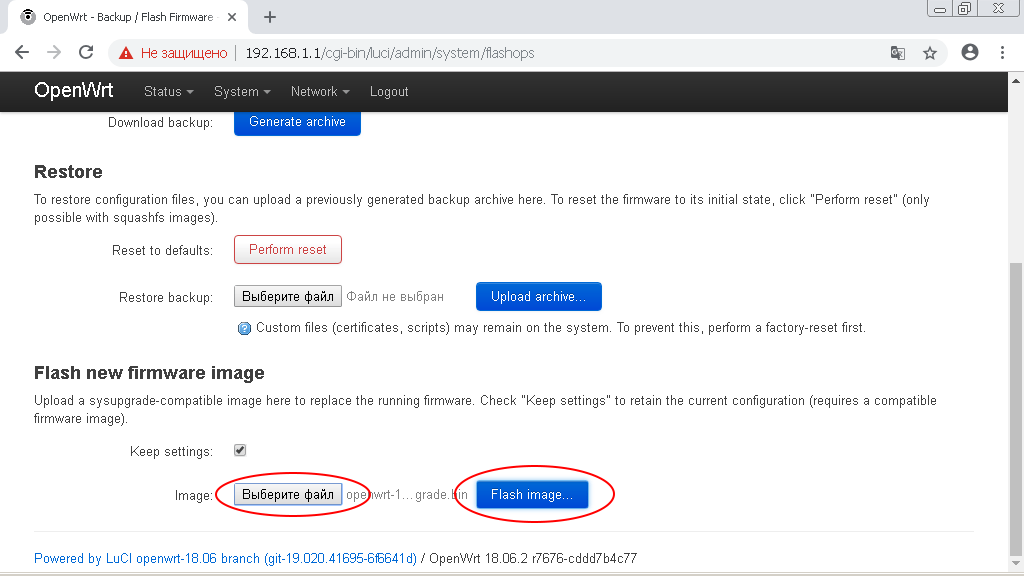
Specify the path to the file whose name ends with "-squashfs-sysupgrade.bin".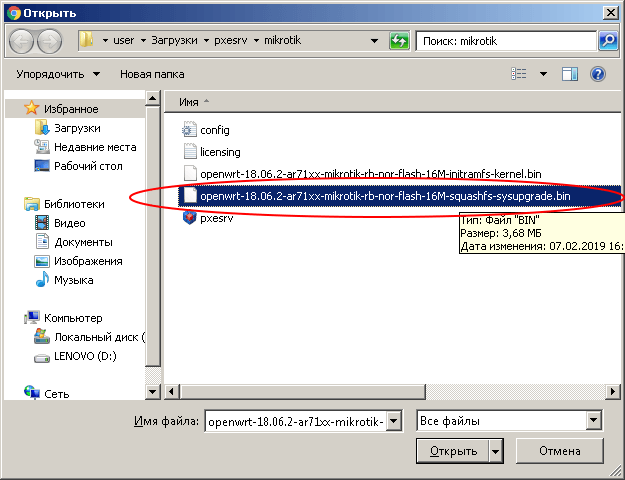
Then click the "Flash Image" button.
In the next window, click the "Proceed" button. The firmware download will start to the router.
!!! IN NO EVENT DO NOT DISCONNECT THE POWER OF THE ROUTER DURING THE FIRMWARE PROCESS !!!
After flashing and rebooting the router, you will receive Mikrotik with OpenWRT firmware.
Possible problems and solutions
Many Mikrotik devices of the 2019 release use a FLASH-NOR memory chip of the GD25Q15 / Q16 type. The problem is that when flashing, the data about the device model is not saved.
If you see the error “The uploaded image file does not contain a supported format. Make sure that you choose the generic image format for your platform. " then most likely the problem is in the flash.
It is easy to check this: execute the command to check the model ID in the device terminal
root@OpenWrt: cat /tmp/sysinfo/board_name
And if you get the answer "unknown", then you need to manually specify the device model in the form "rb-951-2nd"
To get the device model, run the command
root@OpenWrt: cat /tmp/sysinfo/model
MikroTik RouterBOARD RB951-2nd
Having received the device model, we install it manually:
echo 'rb-951-2nd' > /tmp/sysinfo/board_name
After that, you can flash the device via the web interface or using the "sysupgrade" command
Create a VPN Server with WireGuard
If you already have a server with WireGuard configured, you can skip this step.
I will use the MyVPN.RUN application to set up a personal VPN server.
Setting up WireGuard Client on OpenWRT
Connect to the router using SSH protocol:
ssh root@192.168.1.1
Install WireGuard:
opkg update
opkg install wireguard
Prepare the configuration (copy the code below to the file, replace the specified values with your own and run in the terminal).
If you are using MyVPN, then in the configuration below you only need to change WG_SERV - the server IP, WG_KEY - the private key from the wireguard configuration file and WG_PUB - the public key.
WG_IF="wg0"
WG_SERV="100.0.0.0" # ip адрес сервера
WG_PORT="51820" # порт wireguard
WG_ADDR="10.8.0.2/32" # диапазон адресов wireguard
WG_KEY="xxxxx" # приватный ключ
WG_PUB="xxxxx" # публичный ключ
# Configure firewall
uci rename firewall.@zone[0]="lan"
uci rename firewall.@zone[1]="wan"
uci rename firewall.@forwarding[0]="lan_wan"
uci del_list firewall.wan.network="${WG_IF}"
uci add_list firewall.wan.network="${WG_IF}"
uci commit firewall
/etc/init.d/firewall restart
# Configure network
uci -q delete network.${WG_IF}
uci set network.${WG_IF}="interface"
uci set network.${WG_IF}.proto="wireguard"
uci set network.${WG_IF}.private_key="${WG_KEY}"
uci add_list network.${WG_IF}.addresses="${WG_ADDR}"
# Add VPN peers
uci -q delete network.wgserver
uci set network.wgserver="wireguard_${WG_IF}"
uci set network.wgserver.public_key="${WG_PUB}"
uci set network.wgserver.preshared_key=""
uci set network.wgserver.endpoint_host="${WG_SERV}"
uci set network.wgserver.endpoint_port="${WG_PORT}"
uci set network.wgserver.route_allowed_ips="1"
uci set network.wgserver.persistent_keepalive="25"
uci add_list network.wgserver.allowed_ips="0.0.0.0/1"
uci add_list network.wgserver.allowed_ips="128.0.0.0/1"
uci add_list network.wgserver.allowed_ips="::/0"
uci commit network
/etc/init.d/network restart
This completes the WireGuard setup! Now all traffic on all connected devices is protected by a VPN connection.
Links
Source # 1
Modified instructions on MyVPN (additionally available instructions for configuring L2TP, PPTP on the standard Mikrotik firmware)
OpenWrt WireGuard Client
